How to Identify Fake Tech Support Scams: A Comprehensive Guide
1. What are Common Signs of Fake Tech Support?
Fake tech support scams have become increasingly common, preying on users’ concerns over security and technical issues. These scams often masquerade as legitimate technical support but are designed to steal personal information or money. Recognizing the hallmarks of these scams is essential for anyone who uses a computer or smartphone.
Common signs of fake tech support include:
- Unsolicited phone calls or pop-up messages claiming there is a serious issue with your device.
- High-pressure tactics to convince you that immediate action is necessary.
- Requests for remote access to your computer or device.
- Asking for payment, usually via unusual methods like gift cards or cryptocurrencies.
Most authentic companies will not contact you in these ways, and they often provide support through secure channels without charging upfront fees. Fake tech support scams exploit a user’s fear of losing data or having their device compromised, so they may use alarming language or technical jargon to intimidate you into action.
Awareness of these red flags can help you avoid these scams, and most importantly, remember that legitimate tech companies rarely reach out with unsolicited offers of support.
2. How Do Fake Tech Support Scammers Contact Victims?
Fake tech support scammers use a variety of methods to contact potential victims, targeting both personal and professional users. Knowing how these scammers approach their targets can be crucial for prevention.
Typical contact methods include:
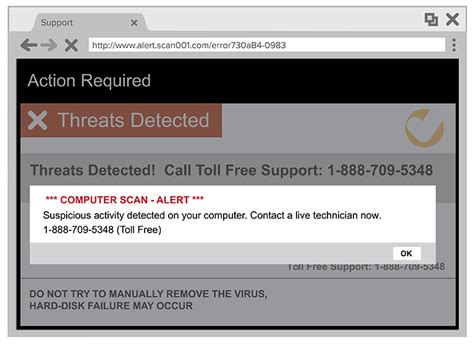
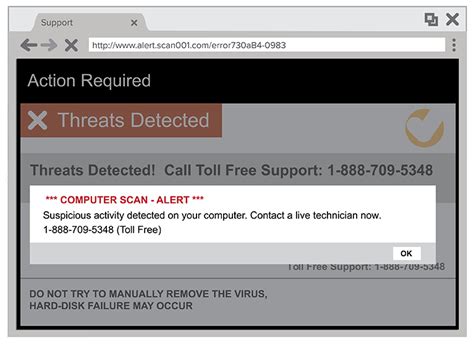
- Pop-Up Warnings: Scammers use fake pop-up warnings on websites that mimic legitimate software alerts. These often claim your computer is at risk and urge you to call a toll-free number for help.
- Phone Calls: Unsolicited calls from individuals claiming to represent well-known tech companies like Microsoft or Apple. They may inform you of supposed security breaches on your system.
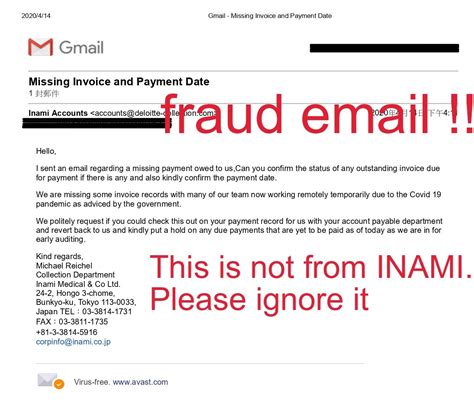
- Email Messages: Scammers send emails pretending to be from trusted companies, warning of suspicious activity on your account.
- Fake Websites: Some scammers create fake websites that mimic legitimate tech support pages, aiming to trick users into sharing sensitive information.
Recognizing these methods of contact is vital. Avoid clicking on suspicious pop-ups and ignore unsolicited calls. Always confirm the legitimacy of any message by contacting the company directly using official contact details.
3. How Can I Verify Genuine Tech Support Services?
Verifying authentic tech support can prevent you from falling victim to scams. Here’s how to ensure that you’re speaking with a legitimate representative:
| Method | Genuine Tech Support | Fake Tech Support |
|---|---|---|
| Contact | Only contacts users who request support. | Often reaches out unsolicited, claiming an urgent issue. |
| Remote Access | Requests permission only after verifying account details. | Requests remote access as a first step. |
| Payment | Does not demand immediate or unusual forms of payment. | Requests payment via gift cards or direct bank transfers. |
Ensure that you’re speaking with a legitimate representative by contacting the company directly through its official website or support number. Avoid disclosing personal or financial details over unsolicited calls.
4. Why is My Computer Showing a Warning Pop-Up?
If your computer displays a pop-up warning that claims to be from a tech support service, it’s likely a scam. These pop-ups often attempt to mimic legitimate warnings from operating systems or antivirus software.
Steps to handle such pop-ups:
- Close the Pop-Up: Avoid clicking any links within the warning, and close it using the task manager if necessary.
- Do Not Call Any Numbers: The number provided is likely part of the scam. Do not reach out to it.
- Run Antivirus Software: Perform a scan with trusted antivirus software to ensure your computer is secure.
Never click on or follow instructions from pop-ups claiming that your computer is infected. Legitimate antivirus software does not usually direct you to call a toll-free number.
5. What is Remote Access and How Do Scammers Use It?
Remote access allows a technician to control your computer from a different location, which can be helpful for troubleshooting. However, scammers misuse this feature to take over your device without your consent.
Scammers use remote access to:
- Install Malicious Software: They can install malware, spyware, or ransomware to steal data or hold your files for ransom.
- Access Personal Files: Remote access allows scammers to browse through personal documents, photos, and other sensitive information.
- Control Browser History: They may manipulate browser settings or history, sometimes blackmailing users based on their online activity.
If someone requests remote access to your computer unsolicited, it’s almost certainly a scam. Avoid granting access unless you have verified the authenticity of the request.
6. How to Identify Fake Emails from Tech Support?
Fake tech support emails often look convincingly real, but there are subtle ways to distinguish them from genuine emails. Here are some indicators:
- Sender Address: Check if the sender’s email address matches the company’s domain (e.g., [email protected]).
- Spelling and Grammar: Scammers often use poor grammar or typos in their messages.
- Urgent Language: Be cautious of any message that urges you to take immediate action.
- Links: Hover over any links to see the URL they lead to before clicking. Genuine companies will use official domains.
Never click on links or download attachments from suspicious emails. Always verify by visiting the company’s official website or calling their customer support directly.
7. Why Do Tech Support Scammers Request Payment in Gift Cards?
Gift cards are difficult to trace, making them a popular payment method for tech support scammers. Scammers ask victims to purchase gift cards and provide them with the codes, which they can then redeem anonymously.
Here’s how it works:
- Demand for Payment: The scammer demands that you purchase gift cards as payment for “services rendered.”
- Code Requests: They ask for the codes on the back of the gift cards, allowing them to access the balance without physical possession of the card.
- Instant Transfer: Unlike bank transactions, gift card payments are instant and non-reversible, making them ideal for scammers.
Legitimate companies do not ask for payment in gift cards. If you’re ever asked to provide gift card codes for tech support, it’s a clear sign of a scam.
8. Can My Computer Be Compromised After a Fake Tech Support Call?
Yes, a fake tech support call can compromise your device if you’ve granted access or installed software. Scammers may use malicious tools to gain further control, steal data, or even install spyware.
Steps to secure your device:
- Disconnect from the Internet: Immediately disconnect to prevent further remote access.
- Run a Full Security Scan: Use reputable antivirus software to scan your system and remove threats.
- Change Passwords: Update passwords for critical accounts like email and banking.
If you’ve interacted with a fake tech support agent, it’s essential to secure your device and seek professional help if necessary.
9. Are Pop-Ups Always a Sign of Malware?
Not all pop-ups indicate malware, but unexpected, recurring ones can be a red flag. Fake tech support scams often use intrusive pop-ups to scare users into thinking their device is compromised.
To distinguish legitimate pop-ups from malware:
- Check Source: Trusted software typically uses clean, simple pop-ups that don’t urge immediate action.
- Close the Pop-Up Safely: If you cannot close a pop-up normally, it could be malicious.
- Run an Antivirus Scan: Performing a scan helps identify if the pop-up originates from malware on your device.
10. How to Report Fake Tech Support Scams?
Reporting fake tech support scams is essential in helping authorities track and prevent future scams. You can report scams in the following ways:
- Contact Your Country’s Cyber Crime Agency: Many countries have online portals for reporting cyber scams.
- Inform Your Bank: If payment was made, notify your bank immediately to help prevent unauthorized transactions.
- Alert the Company Impersonated: Companies can often take steps to protect users once they know their brand is being misused.
Summary Table
| Section | Key Points |
|---|---|
| Common Signs | Unsolicited contact, high-pressure tactics, requests for remote access. |
| Contact Methods | Pop-ups, unsolicited calls, fake emails, and fake websites. |
| Verifying Authenticity | Look for official contacts, avoid gift card payments. |
| Handling Pop-Ups | Close pop-ups carefully, avoid calling numbers, scan your device. |