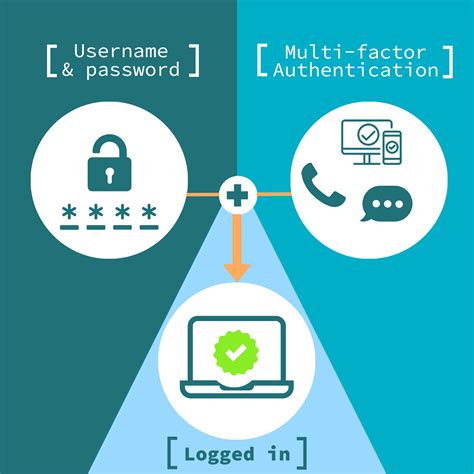
What Does It Mean to Authenticate Data?
Understanding Data Authentication
Data authentication is a fundamental process in the digital world that ensures data integrity, security, and authenticity. It helps verify that data is genuine and has not been tampered with. This section will explore the basics of data authentication, its significance, and methods used in modern technology.
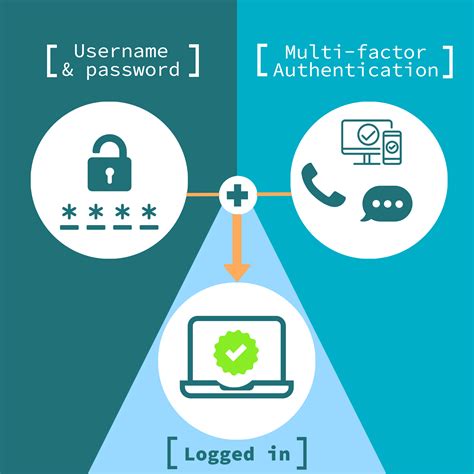
Why Is Data Authentication Important?
In a world where information is exchanged across multiple channels, verifying the authenticity of data is crucial. Data authentication protects users and systems from unauthorized access, fraud, and data corruption. This section outlines the primary reasons why data authentication is a cornerstone of cybersecurity.
Common Methods Used in Data Authentication
There are several methods to authenticate data, ranging from digital signatures to cryptographic algorithms. Each method serves a unique purpose and provides specific advantages for different scenarios. Below is a table that summarizes some of the most common techniques:
| Authentication Method | Description | Usage |
|---|---|---|
| Digital Signatures | Electronic signature validating identity and data integrity | Used in legal documents, emails, and transactions |
| Public Key Infrastructure (PKI) | Framework for managing public key encryption and digital certificates | Used in secure communications and network security |
| Hash Functions | Transforms data into fixed-size hash, ensuring data integrity | Common in blockchain and password storage |

The Role of Cryptography in Data Authentication
Cryptography plays a central role in data authentication by enabling secure communication and safeguarding sensitive data. This section delves into the cryptographic techniques and protocols that strengthen data authentication and enhance cybersecurity.
Challenges in Data Authentication
Although data authentication is essential, it faces challenges such as scalability, key management, and vulnerability to certain types of attacks. This section outlines the primary obstacles in implementing data authentication and how they impact security.
Data Authentication in Blockchain
Blockchain technology uses data authentication to maintain a decentralized, tamper-proof record of transactions. This section explains how data authentication is implemented in blockchain and its benefits for transparency and security.

How Machine Learning Aids Data Authentication
Machine learning is increasingly used in data authentication to detect anomalies and predict potential threats. This section discusses how AI and machine learning enhance data authentication, especially in real-time scenarios.
Real-World Applications of Data Authentication
Data authentication is used across multiple industries, including finance, healthcare, and government. This section provides examples of how data authentication is applied in various sectors to secure sensitive information.
Future Trends in Data Authentication
As technology advances, data authentication methods are evolving to address new security challenges. This section explores future trends in data authentication, including advancements in AI, quantum computing, and biometric security.

Summary Table of Data Authentication Concepts
| Topic | Key Points |
|---|---|
| Importance of Data Authentication | Ensures data integrity, security, and reliability |
| Common Methods | Digital Signatures, PKI, Hash Functions |
| Role of Cryptography | Enables secure data exchanges and enhances authentication |
| Applications | Finance, Healthcare, Government, Blockchain |
FAQ
1. What is data authentication, and why is it important?
Data authentication ensures that information is genuine, unaltered, and verified. It is vital for maintaining data integrity and security across networks.
2. What are the different methods of data authentication?
Common methods include digital signatures, cryptographic protocols, PKI, and hash functions, each suited for specific use cases.
3. How does cryptography support data authentication?
Cryptography secures data through encryption and validation, making it essential for protecting sensitive information from unauthorized access.
4. What role does data authentication play in blockchain?
Blockchain uses data authentication to verify transactions and maintain a decentralized, tamper-resistant ledger.
5. How is machine learning used in data authentication?
Machine learning assists in identifying unusual patterns or security threats, allowing real-time authentication and monitoring.
6. What industries rely on data authentication the most?
Data authentication is critical in finance, healthcare, government, and technology sectors where data security is paramount.
7. What are future trends in data authentication?
Future trends include advancements in AI, quantum-resistant algorithms, and biometrics, aiming to improve security and efficiency.