What Should I Do If I Receive a Suspicious Attachment?
Understanding the Risks of Suspicious Attachments
Receiving a suspicious email attachment can be alarming, especially with the increase in sophisticated phishing and malware attacks. Suspicious attachments are often used by cybercriminals to gain access to your personal information or infect your device with harmful software. This section explains what suspicious attachments are, why they are dangerous, and the types of malware commonly delivered via attachments.
Cybercriminals often disguise attachments to appear legitimate, such as invoices, scanned documents, or purchase orders. Below are some common threats that may come with these attachments:
- Malware: Harmful software like viruses, trojans, and spyware.
- Ransomware: Encrypts files on your computer and demands payment for access.
- Keyloggers: Programs that record keystrokes to steal passwords and personal information.
It’s essential to recognize and avoid these attachments before opening them. Understanding the risks can help you make safer decisions when dealing with unknown emails.

How to Identify a Suspicious Email Attachment
Identifying a suspicious email attachment is the first step in protecting yourself from cyber threats. Various indicators can help you spot suspicious attachments before opening them. Here are some key factors to consider:
| Indicator | Description |
|---|---|
| Unknown Sender | Emails from unknown addresses should be handled cautiously. |
| Unusual File Types | Files with extensions like .exe, .bat, or .vbs are risky. |
| Unexpected Requests | Be wary of attachments asking for immediate action. |
Review the email sender’s details and look for signs of urgency or unusual requests. Identifying these markers can prevent you from opening dangerous attachments.
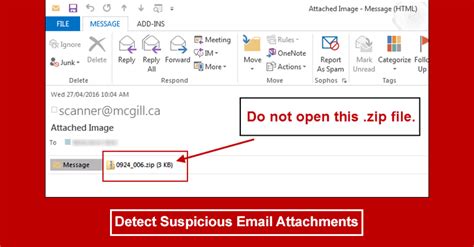
What to Do if You Opened a Suspicious Attachment
If you’ve already opened a suspicious attachment, quick action is crucial. Follow these steps to mitigate potential harm:
- Disconnect from the Internet: Disconnect immediately to prevent any malware from spreading.
- Run Antivirus Software: Use your antivirus program to perform a full system scan.
- Update Security Software: Ensure all security software is up-to-date to handle any potential threats.
- Check for Unusual Activity: Monitor bank accounts, email, and social media for unauthorized access.
Quick actions can minimize the damage from malware or data theft after accidentally opening a harmful attachment.
Steps to Take if You Receive a Suspicious Attachment
Even if you don’t open a suspicious attachment, it’s vital to handle it correctly. Here are some best practices:
- Don’t Download or Open: Avoid clicking on the attachment or downloading it to your device.
- Verify the Sender: Contact the sender through a known channel to confirm if the email is genuine.
- Report Suspicious Emails: Use your email client’s options to report phishing or suspicious messages.

Following these steps can protect your device from potential threats and help prevent the spread of malicious content.
Using Antivirus Software to Scan Email Attachments
Antivirus software can be an effective line of defense against suspicious email attachments. Most antivirus programs offer features to scan email attachments for potential threats. Here’s how you can use antivirus software to scan attachments safely:
- Open your antivirus software and navigate to the email protection or attachment scanning feature.
- Scan the suspicious attachment directly within your email client if your software allows it.
- Regularly update your antivirus definitions to ensure the software can detect the latest threats.
Summary Table
| Step | Description |
|---|---|
| Identify Suspicious Emails | Look for unknown senders, unusual attachments, or urgent requests. |
| Do Not Open Suspicious Attachments | Avoid downloading or opening attachments from unverified sources. |
| Scan Attachments with Antivirus | Use antivirus software to scan attachments before opening them. |
| Take Action if Opened | Disconnect, scan for threats, and monitor your accounts. |
Frequently Asked Questions
How can I identify a suspicious email attachment?
Look for unknown senders, unexpected attachments, or requests for urgent action.
What file types are typically dangerous in attachments?
Be cautious with file types such as .exe, .bat, and .vbs, which are commonly associated with malware.
Is it safe to open an attachment if my antivirus doesn’t detect any issues?
While antivirus software is helpful, it’s not foolproof. Always verify the sender before opening attachments.
What should I do if I accidentally opened a suspicious attachment?
Disconnect from the internet, scan your device, and monitor for unusual activity.
Should I report a suspicious attachment to my email provider?
Yes, most email providers offer options to report suspicious emails, which can prevent future attacks.
Can I use online virus scanners for email attachments?
Yes, many online virus scanners allow you to upload and scan files without downloading them to your device.
How often should I update my antivirus software?
Update it regularly, ideally with automatic updates, to ensure it recognizes the latest threats.



